- To create a firewall rule, follow the steps below. Navigate to Security & SD-WAN Configure Site-to-site VPN. Select Add a rule in the Site-to-site outbound firewall under the Organization-wide settings section of the page. Fill in the desired parameters for the rule. Select Save changes.
- In order to control or restrict access for Client VPN users, firewall rules should be implemented. Layer 3 firewall rules are a powerful tool for permitting and denying Client VPN traffic. Although Client VPN users are considered part of the LAN, network administrators may see a need for limiting overall access.
- Cisco Meraki’s unique auto provisioning site-to-site VPN connects branches securely with complete simplicity. Using IPsec over any wide area network, the MX links your branches to headquarters as well as to one another as if connected with a virtual Ethernet cable.
I’m a long-time user of the Meraki MX security appliance product line. Going way back to the MX-70, I have found tremendous value in what the MX products can do for my far-off sites. (Here’s an old- and I mean old- case study that gets into the early appreciation of the MX line.) I’ve probably set up maybe 65ish total MX devices through the years in multiple states and countries, doing site-to-site VPN, stand-alone, and also some pretty creative configurations. Despite my experience, I was recently reminded that I don’t know it all about a product that I feel extremely comfortable calling myself an expert on.
In one remote site that connects to the main network with site-to-site VPAN, an NTP vulnerability was flagged on a couple of audio visual devices. The device vendor was of absolutely no help (go figure), and our security team asked if we could help from the Meraki side. “Oh sure…” says I. “We got a firewall to leverage.”
Meraki
Cisco Meraki’s unique auto provisioning site-to-site VPN connects branches securely with complete simplicity. Using IPsec over any wide area network, the MX links your branches to headquarters as well as to one another as if connected with a virtual Ethernet cable. Shop the Cisco Meraki MX firewall series to discover the Meraki's advanced cloud based centralized management & network security features. Cisco Meraki MX Firewalls Advanced Cloud-Base Management The store will not work correctly in the case when cookies are disabled.
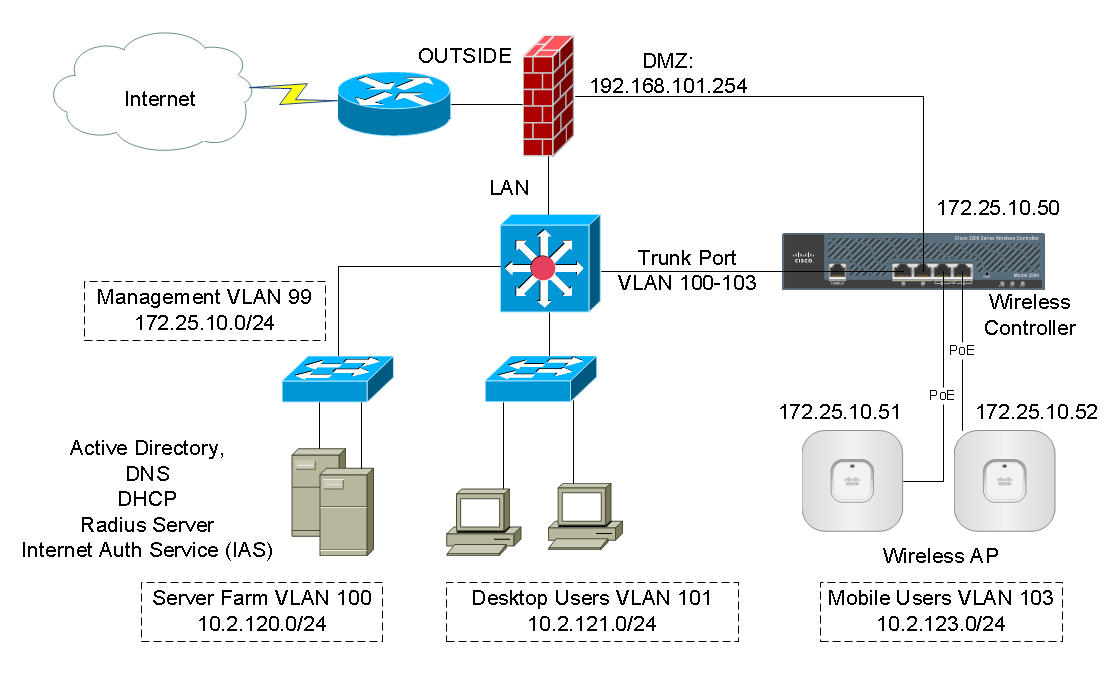
We needed to cabash NTP between the remote site and the main network. I pulled up the Firewall page on the MX and set to work. This is an area in the MX I’ve probably manipulated maybe a couple of dozen times, for everything from stopping phantom ringing on 3rd-party hosted IP phones to simple outbound protocol blocks.
Meraki Firewall Vpn Client
That image represents like three stages of desperation in getting rules right- as nothing I did worked. I simply could not tame the NTP beast to/from the two hosts, and it was making me feel silly. My first inclination was to blame Meraki- surely this stupid box must have issues! Except it didn’t… about the only thing Meraki could have done is perhaps mentioned on the L3 Firewall Page that there is a seperate firewall rule set on the VPN configuration page for site-to-site rules. That looks like this:
I had just never did firewall rules for the site-to-site tunnel. I didn’t know after many years! But I did leverage the Meraki “search our documentation” repository to get educated, with this document that explains it. There’s nothing complicated about it, you just have to know where to find it the first time you need to configure rules for the tunnel versus the Internet edge.
Meraki Firewall Vpn Software
And now you know, too.
